A Statement on two discovered vulnerabilities in Wasabi Wallet
In late July, while working on a basic analysis of bitcoin flows related to the Twitter hack for a planned free OXT Research report, our research analysts discovered two potential privacy vulnerabilities in the Wasabi Wallet software.
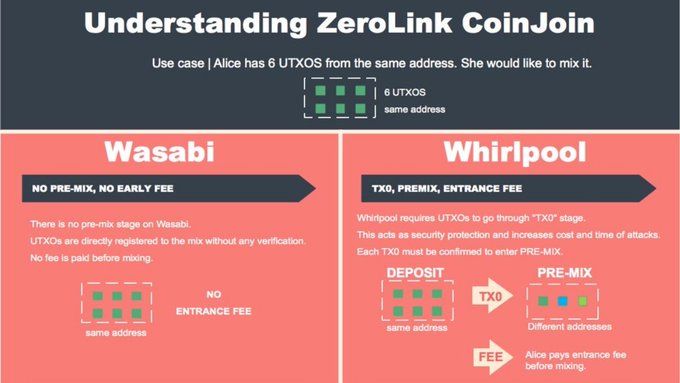
In the past we have found numerous issues with Wasabi Wallet CoinJoin. Those issues always related to mix quality and mix composition as per the metadata left over on blockchain. We never classified those issues as vulnerabilities, just poor design choices.
We began to review the code of Wasabi Wallet in detail, to check if we could identify idiosyncrasies of the architecture allowing us to weaken the anonsets of some mixed outputs potentially controlled by the Twitter Hacker.
The approach used during the assessment of this vulnerability is similar to the one we used for the Toxic Recall Attack previously described for JoinMarket as it leverages additional information based on the CoinJoin algorithm, which is freely available on the zkSNACKs code repository. The vulnerabilities of leveraging additional information about the CoinJoin algorithm has largely been ignored by the Bitcoin privacy community to the detriment of users.
What follows in this statement is:
1) A timeline of events,
2) A general idea of the ramifications of these vulnerabilities
3) Our schedule for releasing the full disclosure publicly.
August 17, 2020
After extensive testing and research we were able to complete our internal analysis and verified the existence of two vulnerabilities that have likely existed since the inception of Wasabi Wallet.
August 18, 2020
It was decided that we should make an immediate private disclosure to the Wasabi Wallet team as we classified these vulnerabilities as Critical.
We marked these as Critical for three primary reasons:
- When a mixed output is remixed, these vulnerabilities break the ZeroLink guarantee for the previous mix, cancelling its benefits.
- These vulnerabilities break a core assumption of mixing, with each remix effectively canceling out the privacy gains of the previous mix.
- These vulnerabilities have been present in the Wasabi Wallet code base for a long time, thus it is likely someone less than ethical has already discovered it and is exploiting it.

We decided to apply a condition to the disclosure schedule in an effort to ensure users were alerted and could make well informed decisions in a timely manner. A user may choose not to use the CoinJoin aspect of the Wasabi Wallet software during the period of time where a solution is still in development, but they wouldn’t be able to make that choice if they weren’t made aware in the first place.
We requested that zkSNACKs Ltd make a public statement within 48 hours alerting users to reported and verified vulnerabilities in Wasabi Wallet, with a vague description of the impact and an official recommendation for users on how they should proceed.
Provided this condition was met, we would keep the disclosure private for 15 days while their team worked to develop and test a patch. Additionally we would provide our suggested mitigations for their development team to explore.
If the condition was not met we explained to them we would alert users on their behalf and follow up with a full public disclosure within 48 hours afterwards.
August 19 12:17AM
Our team sent an email directly to Adam Ficsor (zkSNACKs Founder), Dávid Molnár(zkSNACKs CTO), and a neutral interested third party. We alerted them to our discovery, the ramifications of the vulnerabilities, a verifiable means of reproducing the vulnerabilities, a potential mitigation, and an offer to work together on this issue if it was required.
August 19 10:17AM
Our team received a confirmation from zkSNACKs Ltd CTO Dávid Molnár and were encouraged by his response and promise to look into the details and keep us informed.
August 19 2:58PM
At 2:58PM we received a response from Adam Fiscor which stated they believe we are blackmailing them and they have no interest in pursuing this further with us.
Unfortunately communications have now broken down with no further clarification provided from the zkSNACKs Ltd team.
Disclosure Schedule
We would have preferred that zkSNACKs Ltd handle this disclosure differently, but since the entire disclosure has been flat out denied and our suggested private disclosure schedule was aggressively rebuffed, we are forced to conclude that zkSNACKs Ltd does not consider this a serious issue and therefore we will release the full disclosure publicly in no more than 48 hours.
Recommendation for Wasabi Users
The intention of this statement is to provide enough time for Wasabi Wallet users to seriously consider pausing usage of the CoinJoin aspect of the Wasabi software, if users wish to continue making use of this feature they should consider their reported anonset is *at best* equal to the anonset of the last mix that generated the UTXO.
Recommendation for zkSNACKS Ltd.
Please reconsider your initial response. Now that the public is aware that vulnerabilities have been discovered it is not too late to change your mind and reopen dialog with our team. We are willing to revert to the 15 day public disclosure if you are willing to investigate and mitigate the reported vulnerabilities during that time.



Member discussion